
In a recent landmark case, Singapore authorities sentenced South Korean national Kim Taek Hoon to 5 years’ imprisonment for orchestrating a sophisticated money laundering operation involving over SG$1.55 billion (approximately USD1.15 billion) in illicit funds. Between 2014 and 2017, Kim systematically converted smuggled cash into nearly 28 tonnes of gold bars, which were then exported through falsely declared shipments to evade detection.
Click here to read the full story
This case exemplifies the complexities of trade-based money laundering (TBML) and highlights critical vulnerabilities within the designated non-financial businesses and professions (DNFBPs) sector, particularly for entities handling high-value transactions and cross-border trade activities.
This article uses this case as a comprehensive case study to analyse this trade-based money laundering scheme, highlight vulnerabilities in Anti-Money Laundering and Countering the Financing of Terrorism (AML/CFT) frameworks, and present practical mitigation strategies for Designated Non-Financial Businesses and Professions (DNFBPs).
Money-Laundering Layering Process
This case illustrates a classic layering (within the three-stage money laundering process) by disguising illicit fund flows using trade.
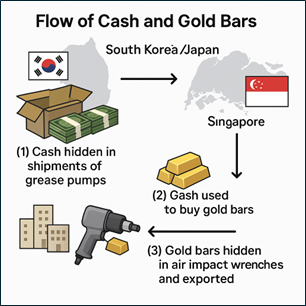
First, cash, hidden in grease pumps, was shipped from South Korea and Japan to Singapore over a 4-year period between 2014 and 2017. Each shipment contained 3 to 4 grease pumps stuffed with at least USD200,000 cash.
The cash was then used to purchase almost 28 tons of 1-kg gold bars from a jewellery wholesaler over a period between 2015 and 2017.
The gold bars were then hidden in air impact wrenches and exported back to South Korea and Japan. At least 239 exports were arranged by three companies registered in Singapore. The owner of these three companies was a friend of the perpetrator, and he did not know that the exports were actually gold bars.
By changing asset form (converting illicit cash to gold bars), moving value geographically (between South Korea, Japan and Singapore), and adding transactional complexity (using disguised air impact wrench exports), the scheme was clearly intended to frustrate tracing of the source of funds before the funds would be integrated back into the legitimate economy.
AML/CFT Vulnerabilities for DNFBPs
- Cash Anonymity
Large, unreported cash enables untraceable fund placement, often converted to assets like gold. - High-Value Products Misuse
Gold’s liquidity and value make it ideal for layering illicit funds, especially without source of fund verification. - Trade-based money laundering
Abuse of legal entities for trade across jurisdictions with unclear purposes aid layering and integration of illicit funds.
Risk Mitigation Strategies for DNFBPs
While detecting trade-based money laundering in layering activities is not easy, there are some control measures that can be taken to mitigate the risks:
For Dealers in Precious Metals and Stones:
- Enhanced Due Diligence for Cash Sales
In this case, the gold bars were purchased from a jewellery wholesaler. As a dealer in precious metals and stones, it can implement stricter verification of cash sources and customer identities for high-value transactions.
During the onboarding, the wholesaler can also understand the purpose of purchasing the gold bars. If the purpose of the purchase does not corroborate with the profile of the customer, it is a clear indication of a suspicious transaction.
Understanding the purpose of purchase during onboarding will be useful during subsequent monitoring of the customer. - Continuous Monitoring
The jewellery wholesaler can also monitor the volume of purchases over time to detect “smurfing”, where purchases are spread across multiple transactions to avoid detection. If the customer made several purchases that does not corroborate with the known sources of fund recorded during earlier due diligence performed, it is a clear red flag for suspicious transactions.
For Accountants and Corporate Services Providers:
- Understand the Nature of Business
In this case, the exports were arranged by three companies registered in Singapore. Accountants and corporate services providers provide compliance services to companies.
During onboarding customer due diligence, it is important to understand the nature of business of a customer. This means documenting the customer’s products and services, main markets served, counterparties in the business and the expected trade volume. By asking these questions to the customers, the accountant or corporate service provider can easily detect if the customer is operating a real business or is just using the business as a mask for other illicit purposes. Understanding the nature of business will also help in subsequent monitoring of the business relationship with the customer. - Continuous Monitoring
Accountants and corporate service providers can review their customers regularly to ensure that the information recorded about the nature of business during onboarding is still valid. Unusual increase in sales turnover or profit should warrant further review on the business activities. Such reviews could include gathering documentary proof from the customer on top trades in the business to understand the products or services delivered and the counterparties involved. If the transactions do not seem to have any economic value or does not corroborate with the nature of business (e.g. exporting air impact wrench when the business nature of business is not in this trade), it should trigger a suspicious transaction report.
Empowering DNFBPs with SentroWeb AML/CFT Solutions
In sophisticated schemes like the gold export case above, DNFBPs, especially for those handling high-value assets and cross-border transactions, face significant risks. SentroWeb AML/CFT Solutions equips businesses with robust tools to combat money laundering activities while ensuring compliance and operational efficiency.
Key Features Tailored for DNFBPs:
- Name and Photo Screening: Screens global watchlists, PEPs, sanctions, and adverse media, checking geographic links and associates to uncover risks.
- Ongoing Monitoring: Tracks and gets flags on the changes in customer risk profiles, ensuring proactive risk management.
- Relationship Diagram Visualisation: Maps company and cross-organisational networks for clear visualisation of complex connections.
- Customer Due Diligence (CDD) with Audit Trails: Streamlines CDD with automated document generation and audit-trailed records, supporting STR filings.
Click here to explore SentroWeb AML/CFT Solutions and book a free demo tailored to your needs today.
Conclusion
This case exemplifies how trade can be exploited in the layering stage of money laundering to obscure the origins of illicit funds. By converting cash into gold, concealing the gold within industrial equipment, and routing it through legitimate trade channels across multiple jurisdictions, the perpetrators effectively introduced multiple layers of complexity to hinder detection and tracing.
The case also underscores key vulnerabilities for DNFBPs — particularly in sectors dealing with high-value, easily transferrable assets like gold — where anonymity in cash transactions and insufficient scrutiny of business activities create opportunities for misuse.
Strengthening due diligence, verifying the legitimacy of cash sources, and maintaining ongoing monitoring of customers and business activities are essential to mitigating these risks. Enhanced awareness and vigilance, with leverage of the right technology tools, like SentroWeb, can help dealers in precious metals and stones, accountants, and corporate service providers identify red flags early, ensuring that legitimate trade channels are not exploited to facilitate the movement and integration of illicit funds.
Recent Posts:
- AML/CFT Case Study: Money Laundering Through Gold Bars and Trade – Vulnerabilities and Risk Mitigation for DNFBPs
- Navigating AML/CTF Compliance in Australia: A Guide for Tranche 2 Entities Under the Amendment to the AML/CTF Act Effective 2026
- The New Corporate Service Providers Regulations and Guidelines: Top 3 Requirements and Compliance Steps CSP Need to Know



